In this dynamic and thriving digital age, cybersecuritycybersecurity has never been more important to your business. Businesses’ reliance and adoption of Information Technology (IT) to gain competitive advantage has been increasing over the last decade as technology progresses and matures rapidly. Business processes generate and process data, transforming them into information and knowledge and, ultimately, generating value for the enterprise. The diagram below shows the cycle of an Enterprise Information Cycle.
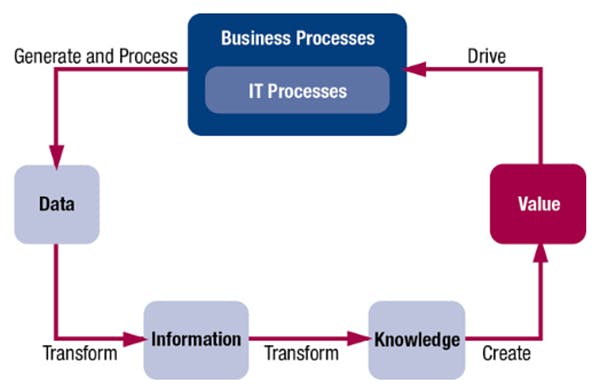
Source: ISACA, COBIT 5, USA, 2012
Essentially, data is transformed into knowledge which creates value for the organization. The output of business processes is data which is critical and important to any organization. In this age, digitized data that are used, processed and stored by applications may be vulnerable to malicious threats that threaten the confidentiality, integrity and availability of data.
The diagram below shows that the IT supports and implements various business functions such as eCommerce, productivity and supply chain management.
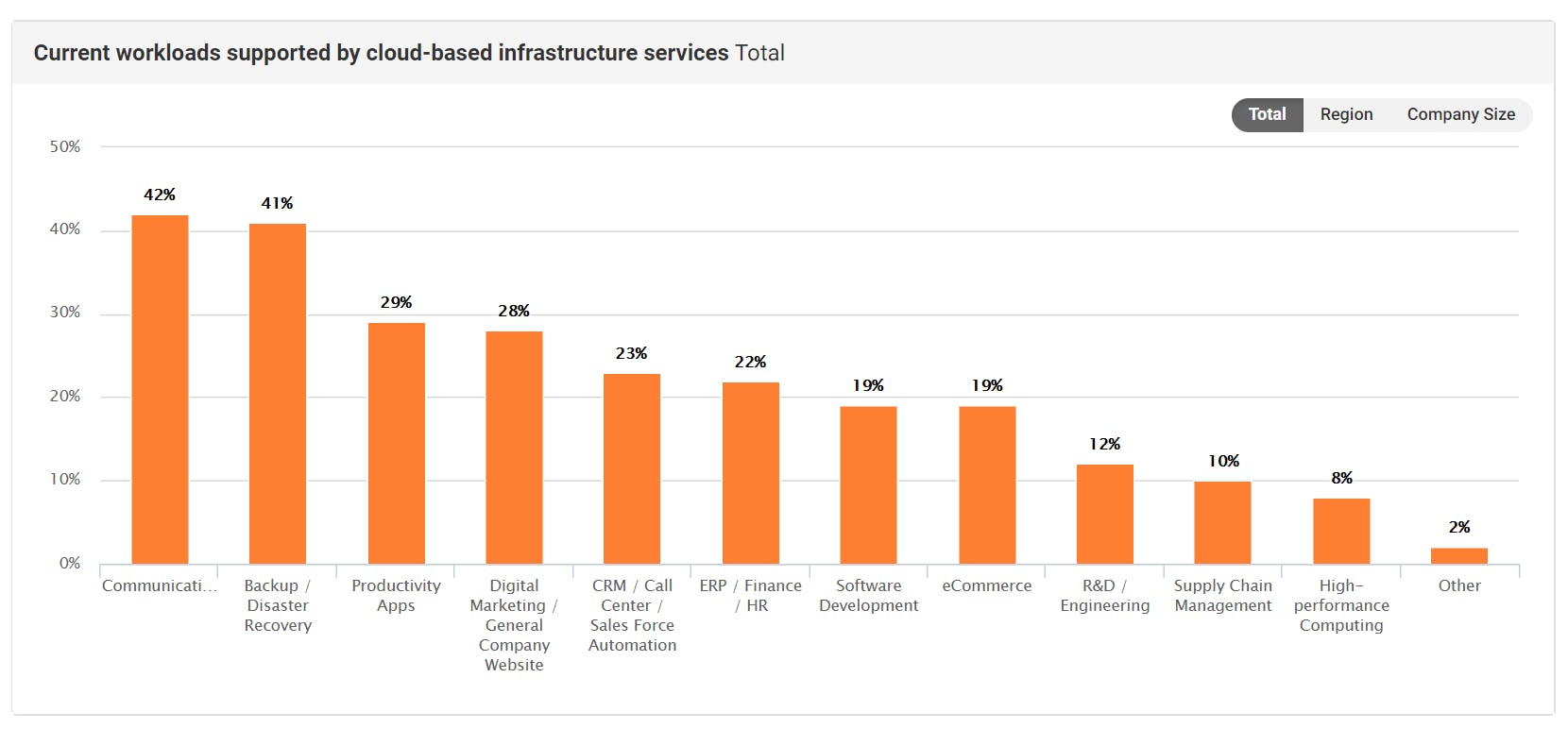
source: https://www.spiceworks.com/marketing/state-of-it/report/
Business Strategy & IT Strategy
The IT strategy of an organization should align to the business strategy to facilitate the achievement of business objectives. In other words, IT plays a crucial supporting role to the business and enables the business to function effectively. This assumption generally holds true to majority of the organisations out there.
It is imperative that the IT function operates optimally and up to management’s expectations. Otherwise, there may be adverse impact to the organisation. Information Security and Cyber Security comes into picture to provide assurance and security to protect data and information assets. Protection is centered around the Confidentiality, Integrity and Availability (CIA) of data.
Information Security & Cybersecurity
Information Security and Cyber Security plays a crucial role to protect the IT assets of an organisation. Accordingly to NISTIR 7298 Revision 2, Cybersecurity is defined as “The ability to protect or defend the use of cyberspace from cyber attacks” while Information Security is defined as “The protection of information and information systems from unauthorized access, use, disclosure, disruption, modification, or destruction in order to provide confidentiality, integrity, and availability”. Cyberspace is defined as “A global domain within the information environment consisting of the interdependent network of information systems infrastructures including the Internet, telecommunications networks, computer systems, and embedded processors and controllers.”.
Organisations cannot afford to ignore the need of cybersecurity as people and businesses are highly interconnected through the Internet. Interconnectivity increases the risk of exposure to threats, incentivizes and motivates malicious attackers to attack vulnerable victims to achieve their goals. Cybersecurity breaches are not a matter of “if” but “when”.
Current State of Cybersecurity
The threat of malicious actors isn’t going to dwine down. According to the State of Cybersecurity 2018, Part 1 published by ISACA, majority of the respondents of the survey thought that they would continue to face even more cyber attacks this year.
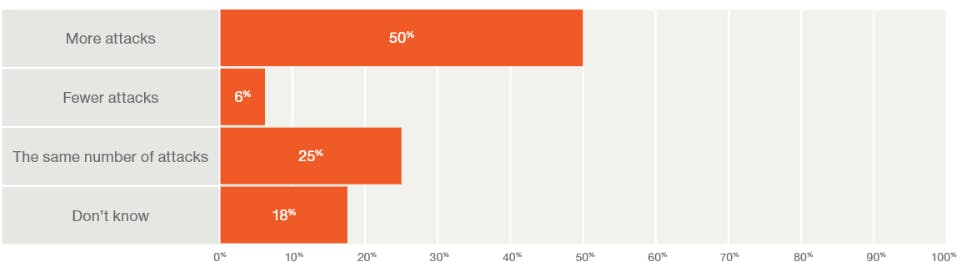
> Survey results by respondents to: “Is your enterprise experiencing an increase or decrease in security attacks as compared to a year ago?”
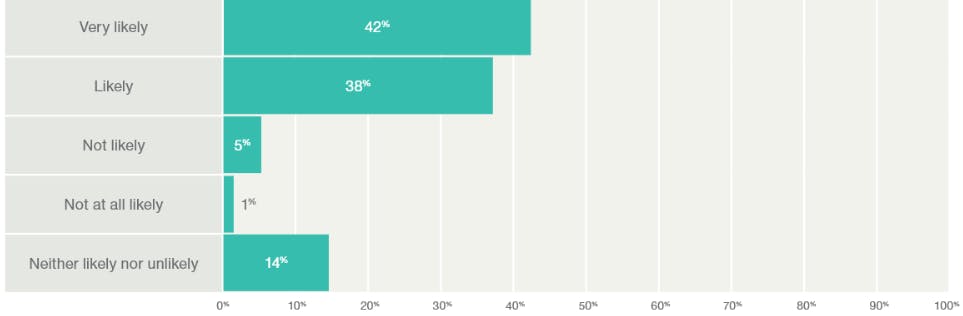
> Survey results by respondents to: “How likely do you think it is that your enterprise will experience a cyberattack in 2018?”
Malicious attackers are quick to adapt and respond to new defensive measures in the industry. Cybersecurity trends are changing to circumvent existing defensive controls implemented by organisations and users. Accordingly to the article 7 cybersecurity trends to watch out for in 2018, there is a prediction and observations of AI-powered attacks, ransomware & Internet of Things, sandbox evading malware and state sponsored attacks.
Beyond the face of Cybersecurity
Cybersecurity is often thought of a means to prevent hackers to gain unauthorized access to systems. The influence of cybersecurity extends beyond that assumption and it is important for organizations to look beyond and understand the full value. The following points described below are not exhaustive.
Assurance and Compliance
Organizations can provide assurance to clients, partners and regulators that security risks are timely assessed and addressed. Organizations may not even be aware of the need for compliance. In certain industries, regulations and laws require organisations to comply to a set of security requirements and data privacy.
Financial and Reputation Loss
Organizations can lose market share and consumer confidence if they experience a successful cybersecurity attack or breach. The damage to the reputation may be very costly depending on many circumstances, such as the location, industry and extent of the impact.
Insider threats
The weakest link in security is often said to be the employee or the human factor. Disgruntled employees and industry espionage are a few of the main risks. Misuse or inappropriate use of the organisation’s systems may also arise that could compromise confidential data.
Shared responsibility
Security is a shared responsibilityshared responsibility of all the stakeholders involved from vendors, clients to employees. Due to the interconnectivity and complexity of information systems, a security compromise in a organization may impact another partner organisation.
Benefits
The importance of cybersecurity has never been higher than before.It is highly recommended for organizations to start today if they have not. Bearing in mind the importance of cybersecurity, it is crucial for organisations to start right with a sound foundation. Although time is of essence, prioritizing speed over quality is often a poor strategy as the cost of change in future is high.
Organizations cannot afford to rest on their laurels and they have to continue to invest in cybersecurity to manage risk in the dynamic landscape, especially given the cost of a cyber attack to a businesscost of a cyber attack to a business. Navigating the cybersecurity domain can be complex when there is a lack of expertise. Organizations can engage a cybersecurity consultants firm to gain access to domain experts based on their needs. Contact usContact us for a discussion about your cybersecurity strategycybersecurity strategy.



