November ended a relatively quiet month with a major security bug in macOS High Sierra. However, there has still been a series of developments and leaks that we at Horangi feel you should be aware of as the year of 2017 comes to a close.
Date: November 28, 2017

Image Source: https://cdn.macrumors.com/article-new/2016/08/012-macos-sierra-970-80-800x449.jpg?retina
MacOS High Sierra Credential Validation Logic Error (CVE-2017–13872)first reported by Lemi Orhan Ergin on twitter, highlighted the ability to login with user ID “root”, and a blank password field after a two authentication attempts.
Upon further investigation, it seems that when a user attempts to login to an account that is enabled, in this case it is the root account, the system creates the account for it with the password supplied. The second authentication attempts subsequently allows access with root and a blank password field. Objective See’s blog has an excellent explanation analysis for this issue, but is summary:
- Logins are handled by the ‘opendirectory’ daemon. The method, odm_RecordVerifyPassword will attempt to read the shadowhash data for accounts upon a login attempt.
- If the account is disabled, the function will fail as the data does not exist, and the function od_verify_crypt_password function will throw an error which goes unchecked.
- Due to the unchecked error, the execution flow proceeds to a method upgrading the entered password (blank) to a shadowhash, which is then saved as the password.
- Upon second authentication, this will succeed.
A patch has been released under Security Update 2017–001, and the issue can also be avoided by setting a password for the account.
Date: November 14, 2017

Image Source: http://cdn2.expertreviews.co.uk/sites/expertreviews/files/2017/08/oneplus_6_rumours_release_date_specifications_1_3.jpg?itok=fY1UmWlc (Accessed December 07, 2017)
Debugging Tool on Oneplus Enabling Root Access. A researcher going by “ Elliot Alderson” found that the EngineerMode app in the OS could allow root level access, and given physical access, can be maliciously used. This application is said to be a diagnostic tool, and not meant to be to be shipped the production copy of the OS. That said, OnePlus has clarified that for the application to be used, USB debugging has to be enabled and physical access available.
More details are available from NowSecure’s research.
Date: November 28, 20017

Image Source: https://www.learnsteps.com/wp-content/uploads/2017/04/Amazon-S3-outage-and-AWS-status.jpg (Accessed December 07, 2017)
AWS’s S3 is in the spotlight yet again. This time for a unsecured bucket containing information labeled “top secret” and “noforn”, with about 100 Gb of data from Army Intelligence and Security Command (INSCOM). The data was in a publicly accessible bucket, which belonged to a third-party defense contractor. This follows recent news of publicly exposed data related to Verizon, U.S.A. Voter records and the Pentagon.
Date: November 26, 2017
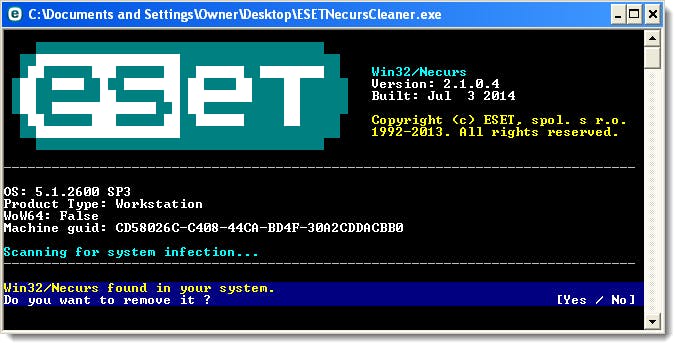
Image Source: https://support.eset.com/Platform/Publishing/images/Authoring/Image%20Files/ESET/KB%20Team%20Only/SOLN3137/SOLN3137FIG1-1A.png (Accessed December 07, 2017)
Necurs Sends Scarab Ransomware at 2 Million emails Per Hour, totaling 12.5 million in 6 hours. Security firm Forcepoint The email comes in the form of a visual basic script with subject lines:
- Scanned from Canon
- Scanned from Epson
- Scanned from HP
- Scanned from Lexmark
No specific amount was stated for decryption of the files, instead, it is written that price depends on the response speed of the victim.
Date: November 24, 2017

Image Source: https://s.imgur.com/images/logo-1200-630.jpg?2 (Accessed December 07, 2017)
Imgur compromised in 2014 with username and password hashes of 1.7 million user accounts (out of approximately 1.7 million accounts) affected. The breach was discovered when a researcher sent the stolen data for verification.
Date: November 21, 2017

Image Source: https://northcoastcourier.co.za/wp-content/uploads/sites/73/2016/11/uber-calle1-960x623.jpg(Accessed December 07, 2017)
Uber compromised in October 2016 with personal data of 57 million users affected. The company had paid the hackers $100,000 ransom to delete the data and hide knowledge of the breach. Only names, emails and mobile numbers are said to be affected. The breach was reported by Uber only after being reported by Bloomberg.
Horangi will be publishing a follow up article regarding the Uber incidnet over the following weeks.
Date: November 21, 2017

Image Source: http://laptoping.com/gpus/wp-content/uploads/2017/01/Intel-HD-620-Graphics.jpg (Accessed December 07, 2017)
Millions of devices using Intel CPUs affected by Buffer Overflow issues allowing privilege escalation (CVE-2017–5708), (CVE-2017–5711).Devices using Intel Manageability Engine Firmware version 11.0.x.x, 11.5.x.x, 11.6.x.x, 11.7.x.x, 11.10.x.x and 11.20.x.x are affected. The system operates separately from the Operating System (OS). Which can be exploited as long as the system is powered and connected to the network.
Date: November 14, 2017

Image Source: https://cdn57.androidauthority.net/wp-content/uploads/2015/01/Microsoft-Office-logo-Android-710x307.jpg (Accessed December 07, 2017)
17-year old Code Execution vulnerability discovered in MS Office (CVE-2017–11882). The DDE feature was found to have a remote code execution vulnerability, allowing unauthenticated remote malicious users to execute code after a malicious document is opened. The file in question, EQNEDT32.EXE, was first introduced in Microsoft Office 2000 and kept for backwards compatibility since.
Date: November 9, 2017

Image Source: https://cdn3.img.sputniknews.com/images/103428/90/1034289094.jpg (Accessed December 07, 2017)
Wikileak releases source code for CIA’s malware control system. Project Hive, a remote command and control server that used to communicate with deployed malware and designed to escape detection, had its source code and details leaked. Investigations revealed that fake digital certificates attributed to Kaspersky Lab were used.
Date: November 7, 2017

Image Source: http://www.the-blockchain.com/wp-content/uploads/2016/03/Ethereumpic1.png (Accessed December 07, 2017)
Flaw in Ethereum Parity Wallet causes $280 million worth of Ethereum to be locked up. GitHub user, “devops199” accidentally removed library code which made multi-sig contracts into regular wallet addresses and assigned to user as its owner. Accidentally calling < initWallet() > and < kill() >, he took ownership of the library and self destructed it, causing all Parity multi-signature wallets to become useless and lose its value.
As we round off into the first week of December, we are reminded from this month’s discoveries that our already technologically dependent world has just gotten bigger and more valuable to the bad guys. Despite the month being relatively quiet, we still cannot be complacent when it comes to our cyber security. With more technological solutions coming into view, we must remain vigilant. Even during the hours of peace.



