The last quarter of 2018 has not been the best for companies, as far as cybersecurity is concerned.
In December alone, the international hotel chain, Marriott Hotel, experienced a breach that exposed the personal information of as many as 500 million of its customers, including the details of their payment information.
Joining the ranks of the unfortunate organizations was the Q&A platform Quora, whose brush with attackers exposed the information of 100 million users.
With these massive amounts of stolen data, customers were suddenly left vulnerable to their data being used by attackers to gain unauthorized access. One such type of attack is called credential stuffing.
What is a credential stuffing attack?
Credential Stuffing is an emerging form of attack that uses automated scripts to try out username or password pairs to gain access to a system. This is however not to be confused with a brute force attack, since unlike the former, no guesswork is being done in credential stuffing.
Why is this attack so effective? A survey done by Keeper Security has discovered that of the 1000 users they surveyed, as much as 83% of them reuse the same password across multiple sites.
In other words, one password acts as a skeleton key for the rest of the locks.
How does a credential stuffing attack work?
The first thing an attacker needs to execute this kind of attack is to get a list of usernames and passwords from sources like a breached system or a password dump site. They then use an account checker to test stolen credentials against multiple websites.
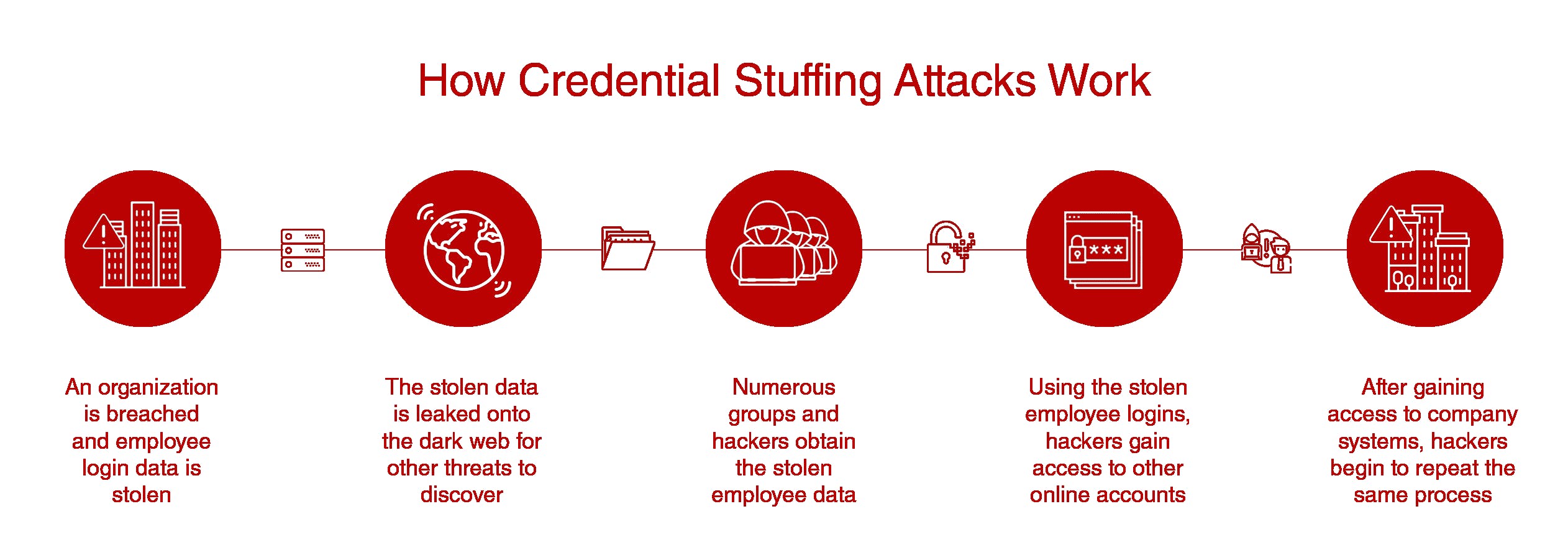
Image source: https://heroic.com/credential-stuffing-threatening-companies/
Once they manage to get a successful login, the attacker then gains access to the account and extracts personal information from them. They may also use the information for other purposes like sending spam and other kinds of transactions like passing it over to other attackers, or selling them on the Dark Web.
What’s there to lose after an attack?
According to a report by anti-fraud specialist Shape Security, the time that lapses between the day credentials are compromise and the day the breach is reported can go for an average of 15 months. That is a lot of time for attackers to carry out credential stuffing attacks undetected.
Shape Security estimates an average of 232.2 million malicious login attempts per day with a 0.05 percent success rate, or in more concrete terms, there would be 116,106 successful account takeover attacks every day with an average of $400 stolen from an account.
The kind of losses that happen, according to their report, also depend on the industry.
Retail
The US retail industry are known to experience the biggest losses from credential stuffing attacks by as much as US$6 billion each year. In fact, 80-90 percent of retail sites’ traffic are from these types of attacks.
They also happen to be one of the industries most reluctant to enforce security measures, causing users to abandon their shopping carts in favor of a smooth user experience.
Airline
Frequent flyer miles are one of the most valuable assets not usually protected by sophisticated security measures. Since a typical customer logs on to their frequent flyer account less often than their other accounts, it takes much longer for them to discover theft from account takeovers than it does with other sites.
One US airline executive reported that $7 million is spent each year reinstating stolen miles alone, and the industry as a whole loses an estimated US$300 million a year.
Hotel
Due to the lucrativeness of hotel loyalty points, and the infrequency of user logons, as much as 82 percent of hotel website logons could be attributed to credential stuffing attacks. The hotel industry is one where brand loyalty is a crucial portion of the business, which means fraud involving loyalty points means a direct hit to the hotel’s revenue.
Customers who participate in loyalty programs are among the hotel’s highest-spending visitors, and one account compromise could lead to the permanent loss of customers, therefore a more substantial revenue loss over the long term.
Consumer Banking
The banking sector, unsurprisingly, is one of the most lucrative industries for cybercriminals. The median US savings or checking account holds between US$3,000-US$5,000, which is substantially higher than a typical rewards account.
The industry as a whole accumulate as much as US$1 billion in financial losses for a single year due to credential stuffing attacks.
How Organisations can Mitigate Credential Stuffing Attacks
To mitigate credential stuffing attacks, OWASP has proposed the following measures.
- Enforcing multi-factor authentication
- Not using emails as usernames whenever possible
- Using device/browser fingerprinting to enforce additional checks when new devices are seen attempting to login
Organizations can also monitor for indicators of a credential stuffing attack like:
- Multiple attempted logons from the same IP address
- Higher volumes than normal of traffic from unusual sources
- Unusual flow through the site/APIs indicating use of automation
Apart from the measures given above, organizations can also regularly check if a user’s password has been part of a known security breach and disallow that password to be used if they are.
For End-Users
On the end-user level, one can use this site to check if their email address was part of a known compromise.
To prevent password reuse, users can also use password managers that can generate strong passwords on the fly and store them in an encrypted vault. Users should also enforce multi-factor authentication on all their accounts whenever possible.
Say NO to skeleton keys
Like in many things in life, prevention is always better than a cure. Unless one aims for their assets to be a free-for-all for questionable elements to use, don’t give them a free skeleton key.




