Cryptocurrency is, no question, the fastest growing currency in recent years. In fact, the top cryptocurrency exchanges trade as much as US$6.21 billion within 24 hours as of time of writing. In 2017 alone, the value of cryptocurrencies increased by more than 2,700 percent.
What used to be a niche market several years ago is now considered as part of the mainstream. The sudden surge also made it a very strong magnet for hackers and thieves. The most recent among these heists is the CoinCheck breach.
What Happened?
CoinCheck’s press statement states that hackers broke into CoinCheck’s systems at 2:57AM GMT+9 last January 26, 2018. However, the breach was not discovered until nearly 8 hours later at 11:25AM the same day.
According to CoinCheck CEO Yusuke Otsuka, around US$530 million worth of NEM have been sent from CoinCheck’s NEM address.
As to where the money went, blockchain analytics company Blockchain Intelligence Group (BIG) was able to trace some of the NEM tokens to a Vancouver-based exchange where BIG claims that the money was being laundered.
Based on what is already known, the breach was only isolated to CoinCheck’s NEM wallet, to the relief of many traders. The company had also owed to refund the stolen NEM as quickly as possible.
During CoinCheck’s press conference, the company admitted that they had stored most of their NEM currency in a hot wallet, and that the private key for that wallet was stolen. As opposed to a cold wallet, which is kept in a secure storage offline, a hot wallet is stored in a live server, leaving the funds vulnerable to attackers.
According to the CoinCheck team, this was done because “It was hard for us to manage [a] cold wallet.”
They also failed to implement NEM’s multisignature smart contact system, which would’ve added another layer of security to the funds.
It is important to note that CoinCheck is one of the few unregulated, centralized exchanges in Japan. In April 2017, Japanese exchanges are required to be registered with the Japanese government. However, CoinCheck was one of the exchanges who started operations before the registration requirement kicked in, and were thus allowed to operate.
The exchange’s application was submitted on September 2017, and is still pending approval to this date.
Tracing the Funds
On January 29, 2018, NEM Vice President Jeff McDonald, through NEM global communications Director Alex Tinsman, confirmed that all accounts with stolen NEM funds have been tagged by the blockchain.
“We’re basically, actively watching and trying to see what’s going on with these funds and how they’re being moved and thinking about how we’re going to work with exchanges to make sure that everything is going to be okay for our community.”
He also explained that despite the illicit nature of the transaction, it was still on permanent record within the blockchain. Only a hard fork will be able to change the transaction records, which NEM refused to do since the breach was due to CoinCheck’s lack of strong security measures and not due to security issues in the blockchain itself.
McDonald, in a separate interview, also revealed that NEM created a tagging system to ensure that all funds stolen from Coincheck are traced. By tagging stolen funds as tainted, crypto exchanges can verify if stolen NEM funds are withdrawn or deposited to regulated trading platforms.
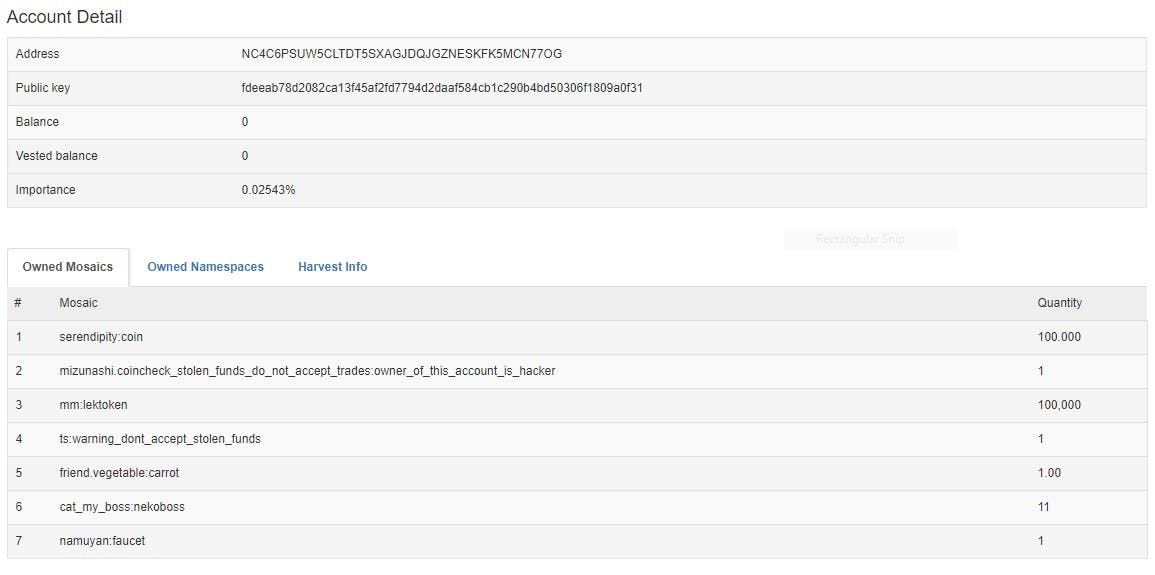
Coincheck has since identified 11 NEM addresses where the stolen coins ended up. Pictured below is an example of one of the addresses in question. Note the tag that says “coincheck_stolen_funds_do_not_accept_trades:owner_of_this_account_is_hacker”
A snapshot of one NEM address where some of the stolen currency ended up. (Source)
Laundering Funds
The Forensic Investigations Division at BIG Blockchain Intelligence Group (CSE:BIGG) have traced NEM tokens to an exchange in Vancouver using their own proprietary software. They will continue to work with law enforcement agencies in Canada and the USA to track the funds, however it remains possible that a large portion of funds have already been laundered.
According to kyodonews.net, about half of the funds may have been laundered anonymously on the “dark web”. A website was setup to facilitate laundering making the recovery process challenging due to the anonymity of converting stolen NEM to private cryptocurrencies, such as zCash and Monero.
Gambling and darknet mixing sites have been the go-to place for laundering cryptocurrency. Various marketplaces, similar to the Silk Road, also provide a means for laundering stolen crypto. Law enforcement agencies around the world have focused their efforts on these marketplaces in their efforts to weed-out laundering activity.
However, given the public availability of transactions, NEM is a less than optimal blockchain technology for criminal actors to wash illicit cryptocurrency.
Restarting Business and Refunding Clients
As early as January 29, the Financial Services Agency (FSA) in Japan ordered CoinCheck to improve its operations and ordered them to submit a report on the breach and any measures taken to mitigate further recurrence.
They also conducted hearings in other exchanges, and if they, over the course of the investigation, found any security weaknesses, they conducted on-site inspections.
CoinCheck on March 12 started to reimburse victims of the NEM wallet breach at the rate of 88.549 Japanese yen (or $0.83) per NEM token stolen. As of March 17, The exchange has already refunded 260,000 affected customers over $440 million from its own funds.
The same day, they restarted trading for various cryptocurrencies like ETH, ETC, XRP, LTC, BCH and BTC. They also dropped support for anonymity-focused currencies Monero, Dash, and zCash
On March 18, the NEM Foundation stopped tracing the stolen coins, since the coins will now be impossible to track two months after the breach took place.
Not the First Crypto Breach
While the CoinCheck breach is the biggest breach in terms of revenue loss, it wasn’t the first to happen in the last five years.
In 2014, Mt. Gox, which once handled as much as 80 percent of the world’s bitcoin trades, filed for bankruptcy after losing bitcoins worth around $500 million. More recently, South Korean cryptocurrency exchange Youbit shut down and filed for bankruptcy after being hacked twice in 2017.
If there’s one thing crypto investors can pick up from the CoinCheck breach and the breaches before it, it’s the importance of keeping the bulk of their currency away from exchanges and into cold storages. For even more tips about keeping coins safe, here are some of them.
One thing is sure: as fast as cryptocurrency is in becoming mainstream, cybersecurity must always be several steps ahead.