Penetration Testing
Is Penetration Testing Sufficient For A Security Audit?
Pentesting may be one of the most popular practices in cybersecurity, but is it the same as a vulnerability assessment and is it comprehensive enough for your organization’s security workflow?
QuanHeng Lim . Aug 16 2019

Penetration Testing
Is Penetration Testing Sufficient For A Security Audit?
Pentesting may be one of the most popular practices in cybersecurity, but is it the same as a vulnerability assessment and is it comprehensive enough for your organization’s security workflow?
QuanHeng Lim . Aug 16 2019

Crypto Security
Securing Bitcoin (or just about any cryptocurrency)
There are many crypto wallet and storage options available, each with their own pros and cons, so we’ve evaluated each option for you! Here’s what we found.
QuanHeng Lim . Feb 23 2019

Crypto Security
Securing Bitcoin (or just about any cryptocurrency)
There are many crypto wallet and storage options available, each with their own pros and cons, so we’ve evaluated each option for you! Here’s what we found.
QuanHeng Lim . Feb 23 2019

Cybersecurity Strategy
Cybersecurity in the Medical Industry
SingHealth, Singapore’s largest healthcare group, was subject to a “deliberate, targeted and well-planned cyberattack”.
QuanHeng Lim . Jul 23 2018

Cybersecurity Strategy
Cybersecurity in the Medical Industry
SingHealth, Singapore’s largest healthcare group, was subject to a “deliberate, targeted and well-planned cyberattack”.
QuanHeng Lim . Jul 23 2018

Penetration Testing
Pentesting Methodology 101
Penetration testing is an authorized simulation of an attack on a system, network, or application to find potential vulnerabilities that can be exploited. Pentesting can be loosely placed into 3 categories, black, gray or white box testing.
QuanHeng Lim . Jun 29 2018

Penetration Testing
Pentesting Methodology 101
Penetration testing is an authorized simulation of an attack on a system, network, or application to find potential vulnerabilities that can be exploited. Pentesting can be loosely placed into 3 categories, black, gray or white box testing.
QuanHeng Lim . Jun 29 2018

Cyber Threats
What's new in Cybersecurity - Feb 2018
We take you through what is new in cybersecurity in the month of February
QuanHeng Lim . Feb 28 2018

Cyber Threats
What's new in Cybersecurity - Feb 2018
We take you through what is new in cybersecurity in the month of February
QuanHeng Lim . Feb 28 2018

Cyber Threats
Preventing .hta Attacks on Microsoft Office
A new Zero-day attack on Microsoft Office affecting all current Office versions on all Windows operating systems was detected by Mcafee and FireEye on 7th April. It is the latest in a long list of exploits; from the “Windows Word Intruder” kit that allowed beginners to create their own version of malware, to the phishing-led Cerber
QuanHeng Lim . Jan 26 2018
Cyber Threats
Preventing .hta Attacks on Microsoft Office
A new Zero-day attack on Microsoft Office affecting all current Office versions on all Windows operating systems was detected by Mcafee and FireEye on 7th April. It is the latest in a long list of exploits; from the “Windows Word Intruder” kit that allowed beginners to create their own version of malware, to the phishing-led Cerber
QuanHeng Lim . Jan 26 2018

Cyber Threats
About Petya/NotPetya
Petya/NotPetya, another ransomware following close on the heels of WannaCry.
QuanHeng Lim . Dec 13 2017
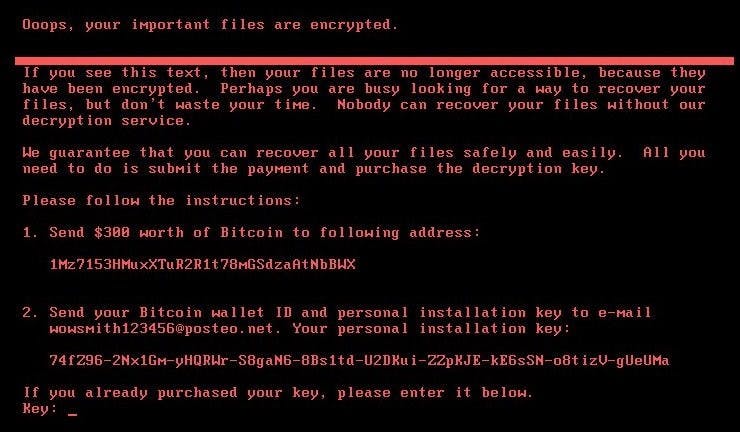
Cyber Threats
About Petya/NotPetya
Petya/NotPetya, another ransomware following close on the heels of WannaCry.
QuanHeng Lim . Dec 13 2017










